A Retrospective of Advanced Installer’s Security Fixes
At Advanced Installer, security is our top priority—we take every necessary step to keep our products secure. When a vulnerability is discovered, we immediately investigate and resolve the issue.
In this article, we outline several vulnerabilities that were detected, explain our investigation process, describe the mitigation strategies we implemented, and provide a timeline from discovery to resolution. Customers who requested early access received fixes ahead of the public release.
Here are some key vulnerabilities we’ve addressed:
Mitigating 7-Zip Remote Code Execution CVE-2024-11477 in LZMA Compression
Summary:
In Advanced Installer, when building an EXE package, users can choose an archive method other than CAB files, such as .lzma compression for their files:

A severe security vulnerability has been discovered in 7-Zip, a popular file compression utility, which allows remote attackers to execute malicious code through specially crafted archives.
This vulnerability, tracked as CVE-2024-11477, has been assigned a high CVSS score of 7.8.
For more details, see Security Advisory 2024-118.
Fix:
The official fix was released in Advanced Installer 22.5 on February 26, 2025.
We addressed the vulnerability in less than two months after it was first reported.
Users who requested early access to a release candidate (RC), containing this fix, received the fix within one month.
Mitigating DLL Hijacking Leading to SYSTEM Privilege Escalation
Summary:
During installation, certain system DLLs are loaded by the setup process for various tasks. For example:
- GdiPlus.dll is loaded during the LanguageDlg action
- Comctl32.dll is used by EXE packages
These DLLs can be exploited for hijacking, allowing an attacker to gain System account privileges.
If an attacker opens a cmd.exe instance and runs the "whoami" command, they will see that the process is running under the System account, even though no administrative privileges escalation has been granted.
While there are several intermediary steps required to execute this exploit, this summary focuses on its impact, rather than the details of how it can be performed.
For a full investigation, see: Investigation and Resolution of .exe.local Directory Vulnerabilities.
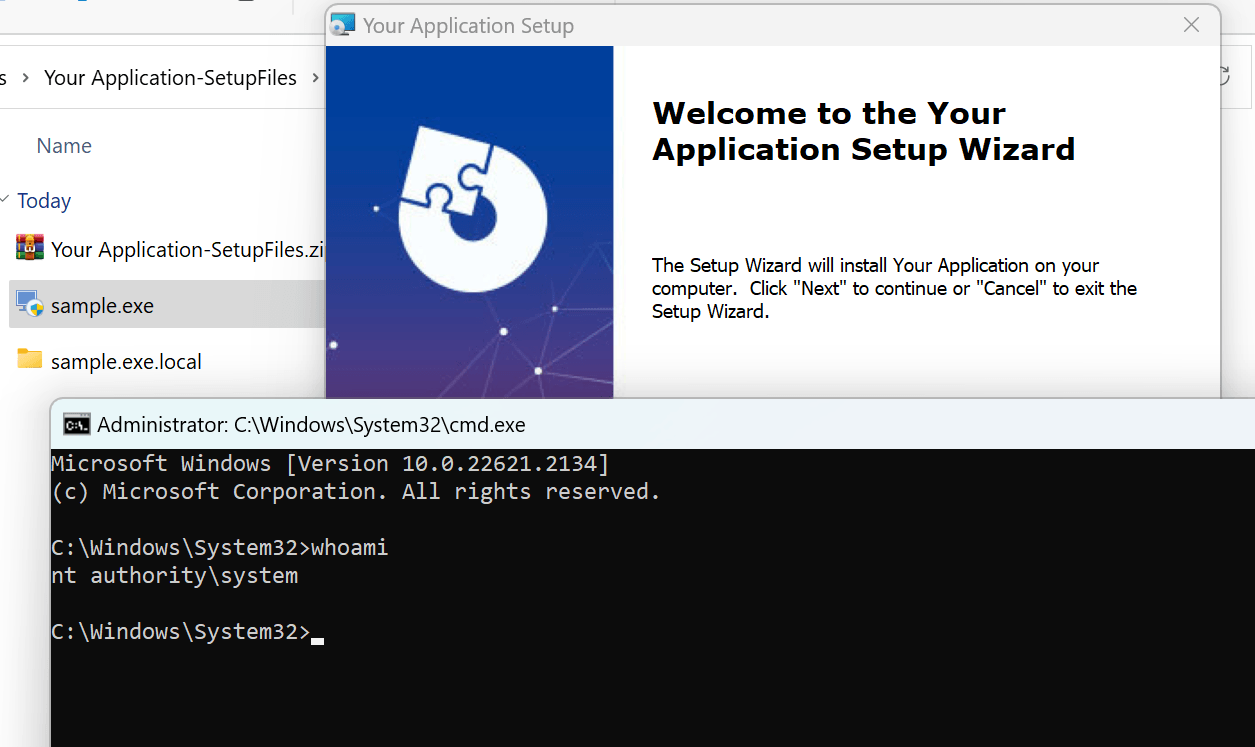
Fix:
Multiple security fixes were implemented, starting with Advanced Installer version 19.7.1 and version 21.1.
Mitigating Security Vulnerability in MSI & CAB Extract Location to Prevent Privilege Escalation
Summary:
A standard user could hijack an MSI used during the installation process by setting an OpLock on:
C:\Windows\System32\msiexec.exe
This prevents the installer from accessing the MSI. Once the OpLock is triggered, the user can overwrite the MSI with any custom MSI, release the OpLock, and the MSI will execute as SYSTEM, resulting in full privilege escalation.
Fix:
We prevented the MSI from being overwritten during installation.
This was fixed in Advanced Installer version 21.0 released on September 5, 2023.
Settings.ais Vulnerability During Repair on advinst.msi - System Privilege Exploit
Summary:
The EXE setup creates a Settings.ais file in:
C:\ProgramData\Caphyon\Advanced Installer\
This file had overly permissive security settings (granting Everyone access) under the SYSTEM context.
An attacker could use a tool like CreateSymLink.exe, to redirect this file to point to a DLL in the Program Files folder (e.g., HID.DLL).
Since this DLL is not present on a default Windows 10 installation, an unprivileged user could modify it.
When the DLL is loaded by a Windows service (triggered via osk.exe and Ctrl-Alt-Del), it runs with SYSTEM privileges, allowing an attacker to gain full control.

A similar vulnerability was reported under: CVE-2021-1079.
Fix:This vulnerability was addressed in Advanced Installer version 20.1, released on November 16, 2022.
Eliminating Local Privilege Escalation Risks in MSI Installer Repair Mode
Summary:
An unprivileged user can trigger the MSI repair process, which runs with SYSTEM privileges but with no elevation prompt to create a temporary file in a user-writable location.
By manipulating this file (using opportunistic locks and symbolic links), an attacker could redirect system operations (such as file deletions) toward critical files. This could allow the attacker to replace or remove important system components and gain full SYSTEM privileges.
More details are available in CVE-2023-25396.
Fix:
This vulnerability was addressed in Advanced Installer version 20.1, released on November 16th, 2022.
Conclusion
Security remains at the core of Advanced Installer’s development process.
We actively monitor potential vulnerabilities, respond swiftly to security threats, and ensure that our users receive timely patches. The examples above highlight our commitment to keeping Advanced Installer safe and reliable.
We encourage users to stay updated with the latest releases to benefit from security enhancements and mitigations. If you encounter any security concerns, please contact us so we can continue improving the security of our products.

