How to sign your package with Azure Trusted Signing or Digicert Keylocker?
This article will guide you step by step on how to use the Custom Sign option to sign your package with tools like Azure Code Signing or Digicert Keylocker.
Update - As of April 2024, Advanced Installer provides built-in integration for Trusted Signing, previously known as Azure Code Signing. For more details please check the Digital Signature page.
Custom signing tools
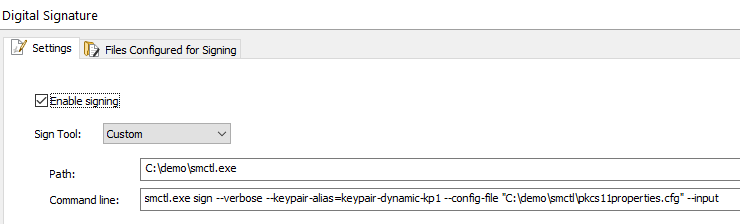
Advanced Installer offers support for using third-party tools like Azure Code Signing or Digicert Keylocker to sign the packages. To achieve this just go to Settings tab from Digital Signature page and select Custom option from Sign tool field.
Signing with Digicert Keylocker
The first step is to specify the path to the executable of the signing tool, in this case, smctl.exe.
Then enter the command line for signing the package. This is the complete list of commands for smctl.exe tool: Signing Manager Controller (SMCTL) command manual. Here is an example:
smctl.exe sign --verbose --keypair-alias=keypair-dynamic-kp1 --config-file "C:\Users\Name\Desktop\smctl\pkcs11properties.cfg" --input
The DigiCert Keylocker signing tool manages command line parameters differently the most
other signing tools, it ignors the first parameter. Therefore in the Command Line field from
Advanced Installer you must include the name or full path of the tool, as in our
example.
The final step is to build the project. The signing tool will be used to sign the package with the specified command line.
Example of workflow for trouble-free signing
The following steps are recommended for signing with DigiCert Keylocker:
- Install DigiCert Keylocker client tool
- Download the certificate
- Create 4 user Environment Variables:
--SM_API_KEY - DigiCert provided API key during certificate creation
--SM_CLIENT_CERT_FILE - Path to the certificate, including name of the certificate
--SM_CLIENT_CERT_PASSWORD - Certificate password
--SM_HOST - DigiCert URL - Add Digicert Keylocker and path to the signing tool :"C:\Program Files (x86)\Windows Kits\10\bin\10.0.22621.0\x64" to System Environment Path
- Restart the server for environment variables to be recognized
- Add a friendly name to certificate after reboot
- Run "smctl healthcheck" to validate the certificate
- Run "smctl windows certsync --keypair-alias= --store=system" to get the certificate added to the local computer, Personal Store.
- In Advanced Installer, use the following settings for custom sign option from Digital
Signature page:
Path: "C:\Program Files (x86)\Windows Kits\10\bin\10.0.22621.0\x64\signtool.exe"
Command Line: "sign /csp "DigiCert Signing Manager KSP" /kc /f /tr "http://timestamp.digicert.com" /td sha256 /fd SHA256"
Signing with Azure Trusted Signing
This method should be used only if the predefined support from Digital Signing page can not be customized as you need.
First, specify the path for the custom signtool you downloaded from Microsoft. Make sure the dependencies required by Microsoft are found in the same folder, next to the signing tool.
Now set the Command Line field as documented by Microsoft. Here is an example:
signtool.exe sign /v /debug /fd SHA256 /tr "http://timestamp.acs.microsoft.com" /td SHA256 /d "Your Application" /dlib "Path to Azure Code Signing Dlib bin folder\x64\Azure.CodeSigning.Dlib.dll" /dmdf "Path to Metadata file\metadata.json"
The Command Line field must not contain the path of the file that
needs to be signed. This path will be automatically appended by Advanced Installer at build
time.